08. Encryption in Transit
Encryption in Transit Heading
Encryption in Transit
ND545 C02 L04 A07 Encryption In Transit Part 1 V2
Encryption in Transit Notes
Recap:
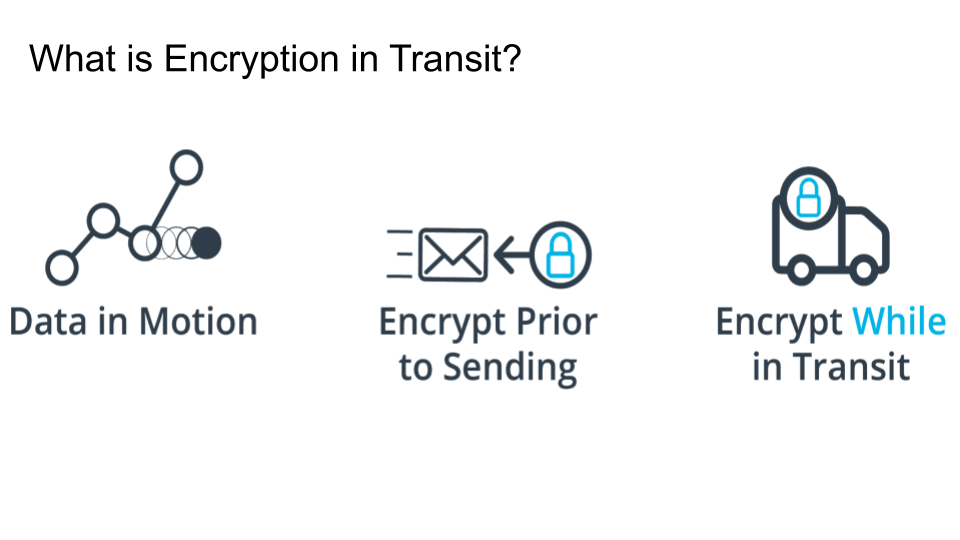
- If data is moving from one location to another, particularly over public internet it is very vulnerable to compromise.
- Either encrypt the data prior to sending it.
- Or encrypt the data while it's in motion. That's what this section is about.
- Data in transit generally uses Asymmetric Encryption and PKI.
- We learned about several common techniques for data in transit:
- HTTPS/TLS HyperText Transport Protocol/Transport Layer Security
- SSH Secure Shell
- SFTP/FTPS Secure File Transfer Protocol/File Transfer Protocol over SSL.
- RDP Remote Desktop Protocol
Key Terms
- Bitlocker: is a full volume encryption feature included with Microsoft Windows.
- Data at rest: means inactive data that is stored physically in any digital form.
- 7-zip: is a free and open-source file archiver, a utility used to place groups of files within compressed, encrypted containers known as "archives".
- Data in transit: also referred to as data in motion, is defined into two categories, information that flows over the Internet and data that flows in the confines of a private network.
Encryption in Transit Heading Image
Encryption in Transit
Choosing the Right Encryption
ND545 C02 L04 A07 Encryption In Transit Part 2
Choosing the Right Encryption
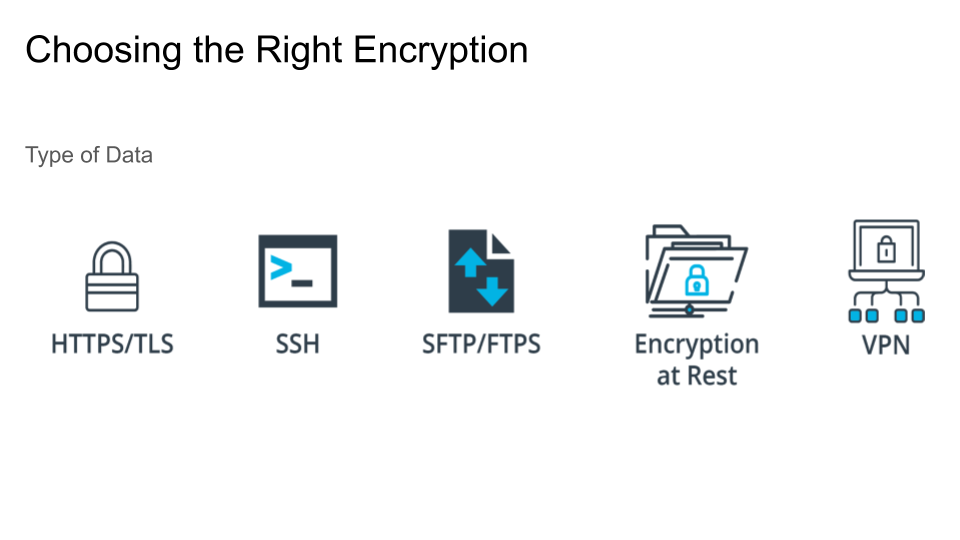
How do you know which encryption method is right for data in transit?
For data in transit, the choices are a bit more clear and based on what you're trying to accomplish.
| Type | Goal |
|---|---|
| HTTP/TLS | Processing or hosting sensitive data accessible from the internet |
| SSH | Hosting servers (particularly Linux) to execute commands and process jobs |
| SFTP or FTPS | Hosting files for others to download (Choice depends on the configuration of the host they reside on) |
| Encryption at Rest | For additional security, consider using on files that are to be accessed via SSH or SFTP/FTPS |
Note: If you recall from a previous lesson it is wise to not have SSH open to the internet, likewise RDP. consider setting up a VPN for those use cases as an additional layer of security.
Choosing the Right Encryption
ND545 C02 L04 A08 Encryption In Transit Walkthrough